Understanding Mutual TLS (mTLS): A Comprehensive Guide for Beginners
Introduction to TLS
Before diving into mutual TLS, let's first understand what TLS itself is.
Transport Layer Security (TLS) is a cryptographic protocol designed to provide secure communication over a computer network. It's the successor to Secure Sockets Layer (SSL) and is widely used for securing web browsing, email, messaging, and other data transfers.
Standard TLS provides:
- Encryption: Protects data from eavesdropping
- Data integrity: Ensures data hasn't been tampered with during transmission
- Server authentication: Verifies the identity of the server
In standard TLS, only the server proves its identity to the client. The client verifies the server's certificate but doesn't need to prove its own identity. This is the model you experience when visiting https websites.
From TLS to Mutual TLS
While standard TLS protects against many threats, it has a significant limitation: it only authenticates the server, not the client. This creates potential security gaps in scenarios where you need to be certain about the client's identity.
Mutual TLS (mTLS) addresses this limitation by requiring both parties to authenticate each other. In mTLS:
- The server authenticates the client
- The client authenticates the server
- Both sides must present valid certificates
This two-way authentication significantly enhances security by ensuring that both parties in the communication are who they claim to be.
How mTLS Works
At a high level, mTLS builds on the standard TLS protocol by adding client authentication to the handshake process. Here's a simplified overview:
- Client initiates connection: The client sends a "ClientHello" message to the server
- Server responds: The server replies with a "ServerHello" message and its certificate
- Client verifies server: The client validates the server's certificate against trusted certificate authorities
- Server requests client certificate: The server sends a "CertificateRequest" message to the client
- Client provides certificate: The client sends its certificate to the server
- Server verifies client: The server validates the client's certificate
- Secure communication established: If both verifications succeed, a secure session is established
This mutual verification ensures that both parties are legitimate and trusted before any actual data exchange begins.
Core Components of mTLS
To understand mTLS thoroughly, you need to be familiar with several key components:
1. Digital Certificates
Digital certificates are electronic documents that bind a public key to an identity. They contain information about:
- The identity of the certificate owner (domain name, organization, etc.)
- The public key
- The digital signature of a Certificate Authority
- Validity period
- Other metadata
Both X.509 and SSL/TLS certificates follow this standard format.
2. Certificate Authorities (CAs)
Certificate Authorities are trusted third parties that issue and validate digital certificates. They serve as the foundation of trust in certificate-based authentication systems.
CAs can be:
- Public CAs: Commercial entities like DigiCert, Let's Encrypt, or Sectigo that issue certificates for public-facing services
- Private CAs: Internal certificate authorities established within an organization for issuing certificates to internal systems
3. Public Key Infrastructure (PKI)
PKI is the framework of policies, procedures, hardware, software, and personnel that creates, manages, distributes, uses, stores, and revokes digital certificates. Components include:
- Certificate Authority (CA): Issues and signs certificates
- Registration Authority (RA): Verifies identities before certificate issuance
- Certificate Database: Stores certificate information
- Certificate Store: Storage location for certificates on end devices
- Certificate Revocation System: Mechanism to invalidate certificates before expiration
4. Trust Chains
Trust chains establish the pathway of trust from an end-entity certificate back to a trusted root certificate. They consist of:
- Root certificates: Self-signed certificates of root CAs
- Intermediate certificates: Certificates signed by the root CA that can issue end-entity certificates
- End-entity certificates: Certificates issued to actual servers and clients
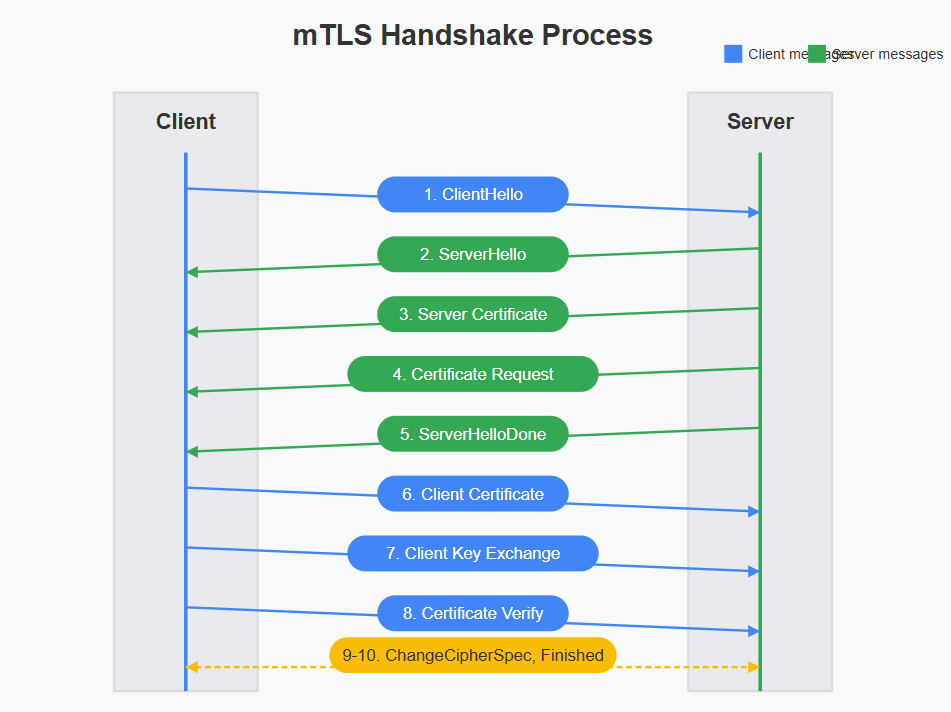
The mTLS Handshake Process
The mTLS handshake is more complex than standard TLS. Let's break it down step by step:
-
ClientHello: The client initiates the connection with a message containing:
- Supported TLS versions
- Supported cipher suites
- Random data for key generation
- Session ID (if resuming a session)
-
ServerHello: The server responds with:
- Selected TLS version
- Selected cipher suite
- Random data for key generation
- Session ID
-
Server Certificate: The server sends its certificate chain
-
Certificate Request: The server requests a certificate from the client, indicating acceptable certificate authorities
-
ServerHelloDone: The server signals it's done with its part of the negotiation
-
Client Certificate: The client sends its certificate chain to the server
-
Client Key Exchange: The client generates and sends information for the pre-master secret
-
Certificate Verify: The client sends a digitally signed message verifying possession of the private key corresponding to its certificate
-
Change Cipher Spec: Both parties indicate they'll start using the negotiated keys
-
Finished: Both parties exchange messages encrypted with the session keys to verify the handshake was successful
If any verification step fails, the handshake is aborted, and the connection is not established.
Benefits of Implementing mTLS
Mutual TLS offers several significant advantages:
-
Strong Authentication: Both parties must prove their identities using cryptographic means
-
Prevention of Unauthorized Access: Only clients with valid certificates can connect to the server
-
Protection Against Various Attacks:
- Man-in-the-middle attacks: Attackers can't easily intercept and modify traffic
- Replay attacks: Each session uses unique keys
- Impersonation attacks: Attackers can't pretend to be legitimate clients without valid certificates
-
Non-repudiation: With certificate-based authentication, parties can't easily deny their participation in the communication
-
Simplified Authorization: Once identities are securely established, authorization decisions become more straightforward
-
Reduced Reliance on Passwords: Certificate-based authentication eliminates password-related vulnerabilities
Implementation Challenges
While mTLS offers robust security, it does come with implementation challenges:
1. Certificate Management Complexity
Managing certificates throughout their lifecycle requires:
- Certificate issuance and distribution
- Certificate renewal before expiration
- Certificate revocation when compromised
- Storage of certificates and private keys
2. Operational Overhead
mTLS introduces additional operational considerations:
- Certificate rotation planning
- Monitoring for expiring certificates
- Handling certificate-related errors
- Emergency procedures for certificate issues
3. Performance Impact
The additional handshake steps and cryptographic operations in mTLS can affect performance:
- Increased latency during connection establishment
- Higher CPU utilization for cryptographic operations
- Additional network traffic for certificate exchange
4. Scalability Concerns
As systems grow, certificate management becomes more challenging:
- Managing thousands or millions of client certificates
- Automating certificate provisioning
- Maintaining revocation lists or OCSP services
5. Client Compatibility
Not all clients support mTLS, particularly:
- Legacy systems with outdated TLS implementations
- Simplified IoT devices with limited cryptographic capabilities
- Third-party systems you don't control
Best Practices for mTLS Deployment
To implement mTLS successfully, consider these best practices:
1. Establish a Robust PKI
- Set up a proper certificate hierarchy with root and intermediate CAs
- Define clear certificate policies and practices
- Implement strong key management procedures
- Consider using hardware security modules (HSMs) for root key protection
2. Automate Certificate Management
- Use automation tools for certificate lifecycle management
- Implement automated monitoring for certificate expiration
- Set up alerts for certificate-related issues
- Consider certificate management platforms for large deployments
3. Plan for Certificate Revocation
- Maintain up-to-date Certificate Revocation Lists (CRLs)
- Implement Online Certificate Status Protocol (OCSP) for real-time validation
- Define clear revocation procedures for compromised certificates
- Test revocation mechanisms regularly
4. Implement Strong Certificate Validation
- Validate the entire certificate chain
- Check revocation status
- Verify certificate attributes (Common Name, Subject Alternative Name)
- Validate certificate purpose and constraints
5. Consider Certificate Pinning
- Implement certificate pinning for critical systems
- Pin intermediate or leaf certificates rather than just root certificates
- Maintain fallback mechanisms for emergency certificate changes
6. Plan for Certificate Rotation
- Define certificate validity periods based on security requirements
- Implement seamless certificate rotation procedures
- Test rotation processes before certificates expire
- Consider automated rotation for short-lived certificates
Conclusion
Mutual TLS provides a robust security mechanism for ensuring both parties in a communication channel are authenticated. While it adds complexity compared to simpler authentication methods, the security benefits often outweigh the implementation challenges for sensitive systems.
As you progress in your IT career, understanding mTLS will prove invaluable when designing secure systems, especially in modern architectures like microservices, zero trust networks, and IoT deployments.
By implementing mTLS with proper certificate management practices, you can significantly enhance your application's security posture and protect against a wide range of attacks.
Remember that mTLS is just one part of a comprehensive security strategy. Combine it with other security measures like proper authorization, input validation, and monitoring to create truly secure systems.
Additional Resources



Comments
Post a Comment